Authorization Policy
An authorization policy defines what resources a user or group can access within an organization. When applying an authorization policy, factors like access management to on-premises or cloud services, authentication flows, and device identity introduce complexity that only scales with organization size.
Pomerium meets you where you are by allowing you to configure granular policies that support or extend your existing policies on a per-route, per-request basis.
Pomerium authorization policy
You can apply policies in Pomerium to Namespaces or Routes.
Namespaces
Administrators can create a namespace, add users, groups, and routes to it, and configure a policy that applies to that specific namespace.
Namespace support is only available for Enterprise customers.
Routes
You can build TLS-encrypted routes to upstream applications and configure policy that restricts access based on the policy criteria.
Pomerium Enterprise and Core customers can configure and apply policies to routes.
Continuous verification
Pomerium continuously evaluates policy on every request.
Policy applied to any route or namespace will enforce authorization checks throughout a session, ensuring that only the intended user with the right context can access a protected resource.
Apply authorization policy
Pomerium offers three methods to configure and apply policies:
Pomerium Policy Language (PPL)
Pomerium Policy Language (PPL) is a declarative, YAML-based access control policy language you can use to configure authorization policies.
PPL is intuitive by design and defines policy with one or more rules composed of actions, logical operators, and criteria. Each criterion has a name and corresponding data.
- Core
- Enterprise
In Pomerium Core, you can build a policy with PPL and apply it to a route in your configuration file:
policy:
- allow:
or:
- email:
is: user@example.com
In this example, only a user with the email user@example.com can access the target application.
In the Enterprise Console, you can use the EDITOR to manually configure policy with PPL:
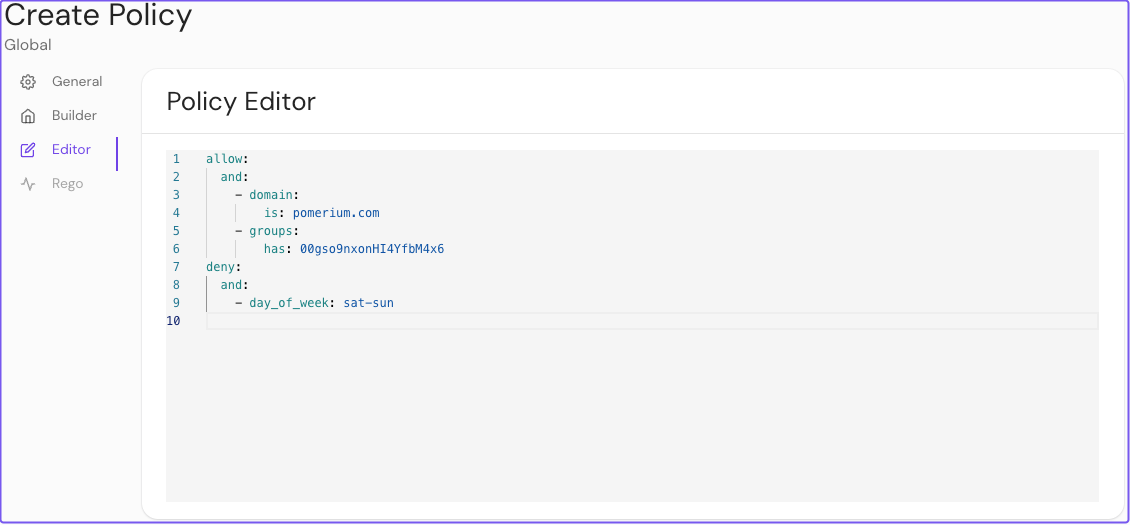
In this example, Pomerium will grant a user access if their email address ends in example.com and their groups ID matches 00gso9nxonHI4YfbM4x6. Pomerium will deny the user access on Saturdays and Sundays.
Enterprise Console GUI
The Enterprise Console provides a policy builder GUI so you can build policies and reapply them to multiple routes and namespaces.
Use the BUILDER tab to build your policy:
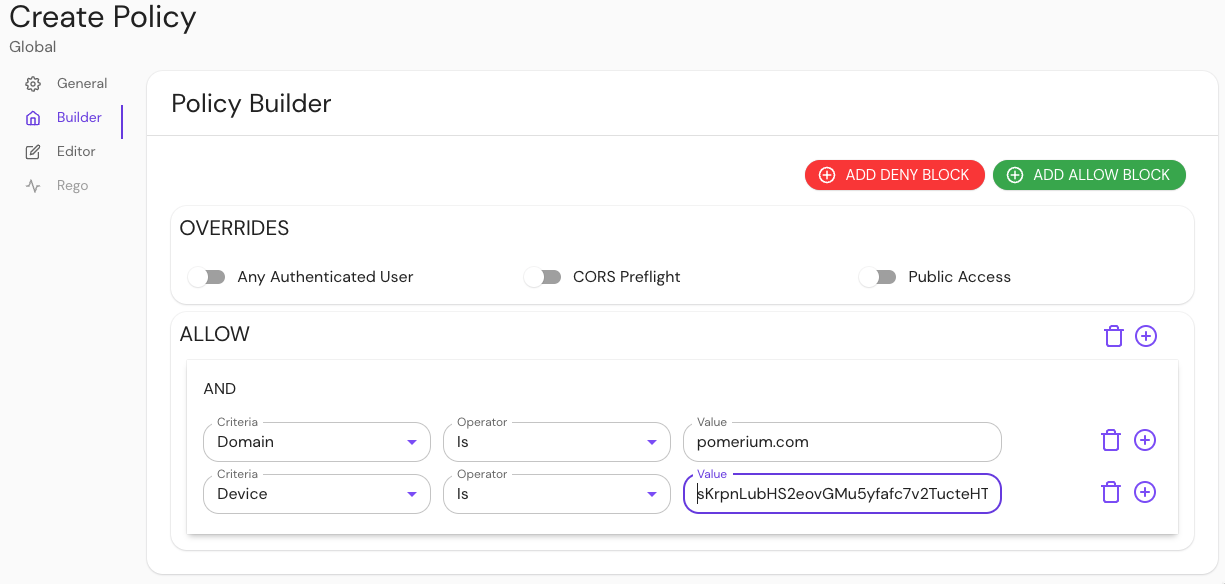
In this example, a user will have access if their email address ends in example.com and their device ID matches the ID in the Value field.
Reapply policies
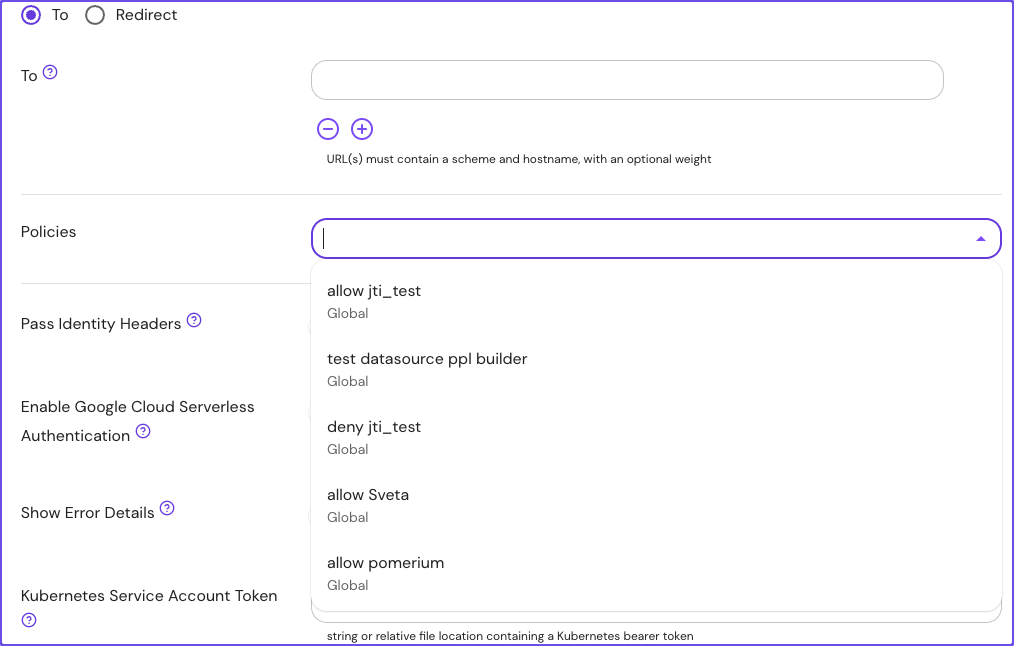
Reapply policies as necessary to any route or namespace:
Rego support
Pomerium Core and Enterprise support policies expressed in Rego for organizations that prefer to use OPA.
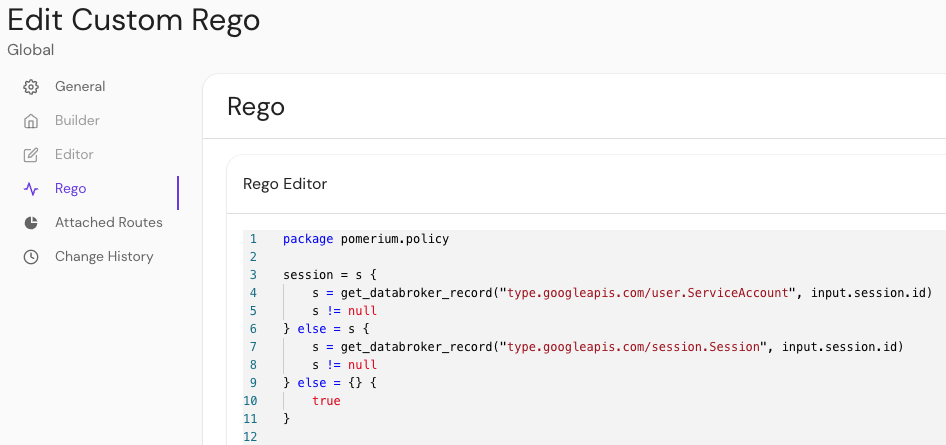
For Enterprise customers, use the Rego tab to configure your policy:
A policy can only support PPL or Rego. Once one is set, the other tab is disabled.
Example Rego Policy
Policy overrides
Pomerium Core and Enterprise offer the following options for overriding your authorization policy:
- Any Authenticated User: Allows access to a route with this policy attached to any user who can authenticate to your identity provider
- CORS Preflight: Allows unauthenticated HTTP OPTIONS requests as per the CORS spec
- Public Access: Allows complete, unrestricted access to an associated route (use this setting with caution)
Manage devices
The Manage Devices feature in the Enterprise Console allows you to enroll and manage user devices for policy-based authorization.
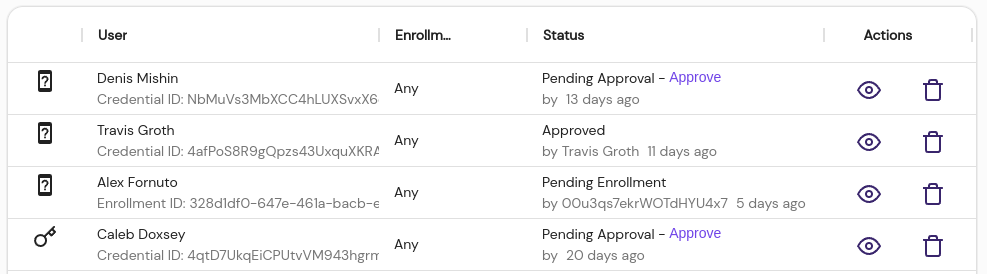
The Devices List displays enrolled devices for each user and the approval status. Administrators can inspect, approve, or delete registered devices from this table.
See Device Identity for more information.